10 Ways to Protect Your Organization Now
Organizations depend on third-party commercial software not only for securing their networks, but also for managing and storing customer data, financial accounting and reporting, and fulfillment of core business processes. Managing the cyber aspects of these software supply chains is an area of critical concern.
What is a Software Supply Chain Attack?
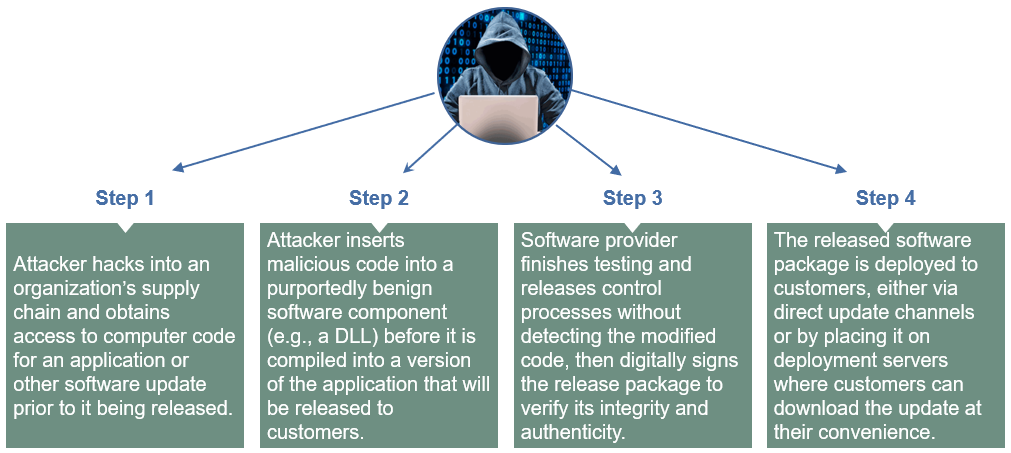
A software supply chain attack involves the infiltration of software developer systems and data. The attacker is able to insert malicious code into a software component that is then compiled into a released software package. The compromised package is then made available to customers of the software provider as an update to the package they are currently using.
Steps in the attack ...
What Makes this Attack so Difficult to Detect?
Attackers using this technique are often highly sophisticated and take special care to avoid detection. Their attack can span multiple months as they carefully assess the target environment, evaluating how best to insert the malicious code that will become a backdoor for later attacks.
Steps that hackers take to hide their activities have included the following:
- Using naming conventions that align with those used by the target company
- Using files names that resemble legitimate Windows files and directories
- Using advanced encryption to make it more difficult to detect the attack
- Turning off event logging during major hacking activities
- Altering network configuration settings to avoid triggering alarms
What is the Potential Business Impact on Customers?
Although the impact on the software company is severe (loss of customer confidence and market share), the impact on the software provider’s customer base is many times greater, as they are the ultimate targets of the attack. Potential financial impact on companies targeted by the malware include:
- Stolen intellectual property
- Stolen customer data
- Disclosure/ransoming of highly sensitive information
- Compromise of key financial systems and unauthorized movement of funds
- Investigative costs to ascertain the scope of the breach
- Costs required to sanitize the IT environment and remove any backdoors
- Impact of public disclosure on stock value and market share
- Cost of lawsuits and potential regulatory actions
- Price increases for cyber insurance or cancellation of policy
What are steps that organizations need to take now?
As we can see, individuals with malicious intent are taking advantage of current weaknesses in the software supply chain to launch attacks and break down defenses. Keeping this in mind, I have identified 10 steps your organization should be taking right now. Here are the first five:
- Supply Chain and Vendor Risk Management – To ensure the integrity of your software supply chain, it is imperative to review your previous vendor risk management (VRM) assessments, and based on their scope and timing, perform a complete vendor cyber risk assessment of your software supply chain. The output of this can then be used to triage the identified critical gaps, develop a VRM improvement plan, ensure VRM governance and oversight, review contracts, and recommend additional protections.
- Zero Trust Architecture – Zero Trust is a security model that should be implemented to reduce your organization's exposure. It requires all users, local and remote, to authenticate, be authorized and validate their security configuration before getting or retaining access to corporate applications, systems, or data. It generally includes technology like multifactor authentication (MFA), identity and access management (IAM), network-segmentation and good endpoint security technology to deter attackers and limit their access in the event of a breach.
- Network Segmentation – As its name implies, network segmentation is splitting a computer network into subnetworks, each one being a separate network segment. It is a huge defense against attackers as it assumes the outer perimeter may have already been breached. This provides several immediate benefits: a) slows down the hackers - makes lateral movement more difficult; b) damage containment - creates "watertight" compartments; c) faster Incident Response - more quickly identify location of attack; d) makes insider attacks more difficult - facilitates zero trust; and e) eases organizational compliance - segregates regulated data.
- Identity and Access Management – It is critical to ensure that only the right people, processes and systems have the right access to the right resources at the right time. IAM is extremely useful in this regard and has technologies (including MFA) that enable granular access control and auditing of all IT assets on premises and in the cloud. It encompasses how individuals are identified in a system; how roles are identified in a system and how they are assigned to individuals; adding, removing, and updating individuals and their roles in a system; assigning levels of access to individuals or groups of individuals; and protecting the sensitive data within the system and securing the system itself.
- Security Operations Center Risk Management – The focus of a SOC is the round-the-clock monitoring, management and operational improvement of the organization's security posture, including prevention, detection, analysis, incident response, and recovery activities. SOC services have evolved from primarily on-premise, to a variety of hybrid delivery models, including on-premise, remote and cloud-based services and staffing, often utilizing VDI and remote enablement to optimize the flexibility and cost. Processes exist for rapid triaging of potential vulnerabilities, evaluation of events, and handling escalation to incident response teams.
In Part 2, I will cover the remaining 5 steps. Together, these 10 steps will help your organization strengthen your security posture, keep a challenging situation from becoming disastrous, and withstand these attacks while keeping essential services running.
Stephen Head, CPA
Director, IT Risk Advisory Services
+1 704 953 6688
stephen.head@jeffersonwells.com
About the Author
Stephen has broad-based experience in cyber risk, regulatory compliance, IT governance and aligning controls with multiple standards and frameworks. He is the author of the internationally recognized Internal Auditing Manual and Practical IT Auditing, both published by Thomson Reuters, and has served as International Chair of ISACA's Standards Board. Stephen is a CPA, CISSP, CISM, CDPSE, CMA, CFE, CISA, CGEIT, CRISC, CBCP, MCSE, CHP, CHSS, CITP, CGMA, CPCU, and holds an MBA from Wake Forest University.
We welcome the opportunity to discuss your needs in this area and share our thought leadership to help your team. www.jeffersonwells.com






Comments